Row Level Security
When setting up a schema in the management console, you can set row level security on groups and/or users. Set groups or users with row level security so they only see the data that’s relevant to them within WriteBackExtreme. Overall, row level security provides a powerful mechanism for controlling access to sensitive data in a database. By restricting access to specific rows based on the identity of the user, you can ensure that your data remains secure and confidential, while still allowing authorized users to access the information they need to do their jobs.
An example is that users in a particular department will only see their departments data. Multiple rules can be set up so groups/users can see their departments information in a particular region for example.
The rules within a policy will be stacked. This means that data is only shown when all conditions are met (AND)
Defining multiple policies for a schema will result into a union (OR)
Multiple entitlements within a user or group will create a union (OR)
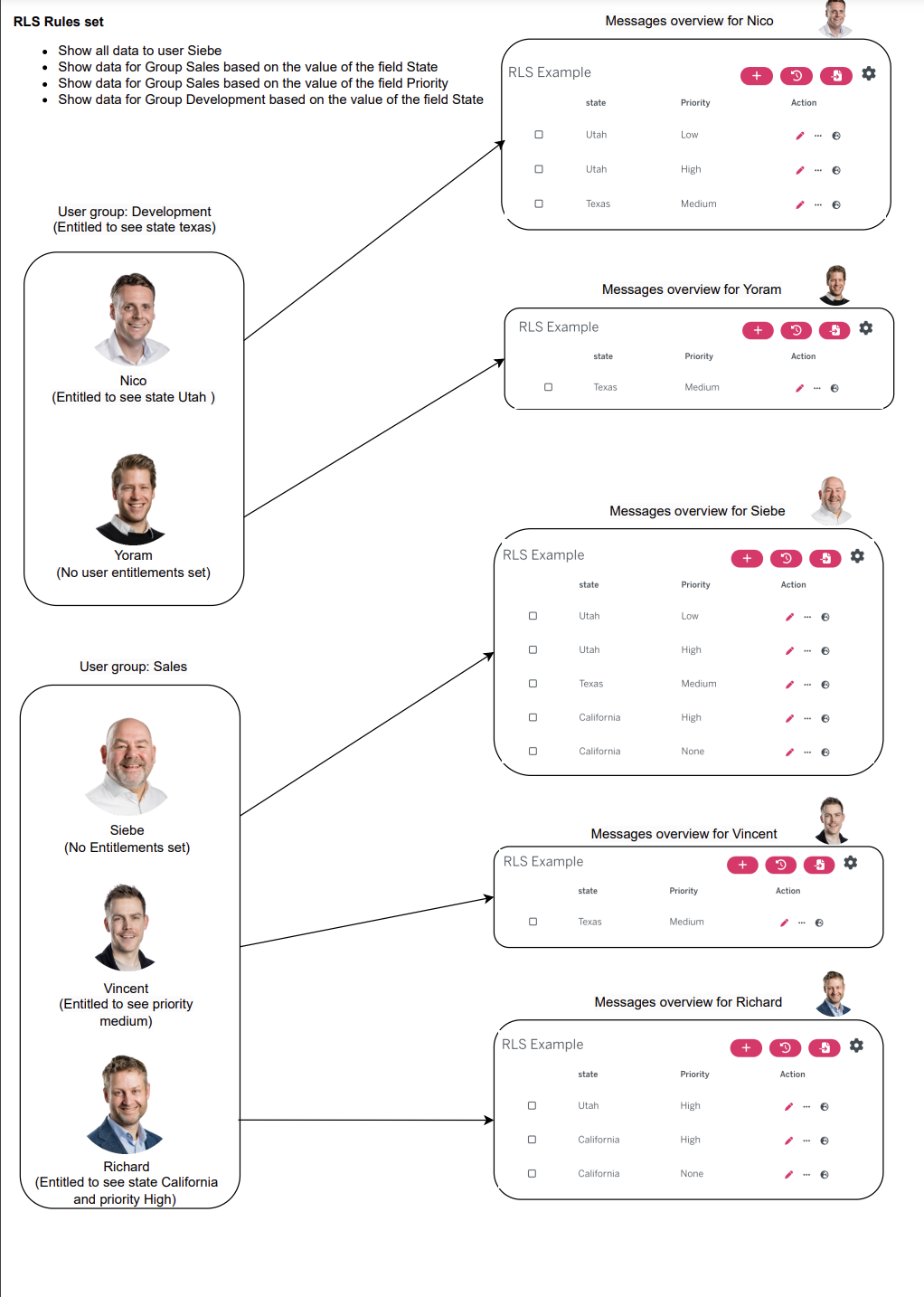
How it works
Choose the entitlements of your user or group and set the value that applies to your schema. The user or group will only see the data within these fields.
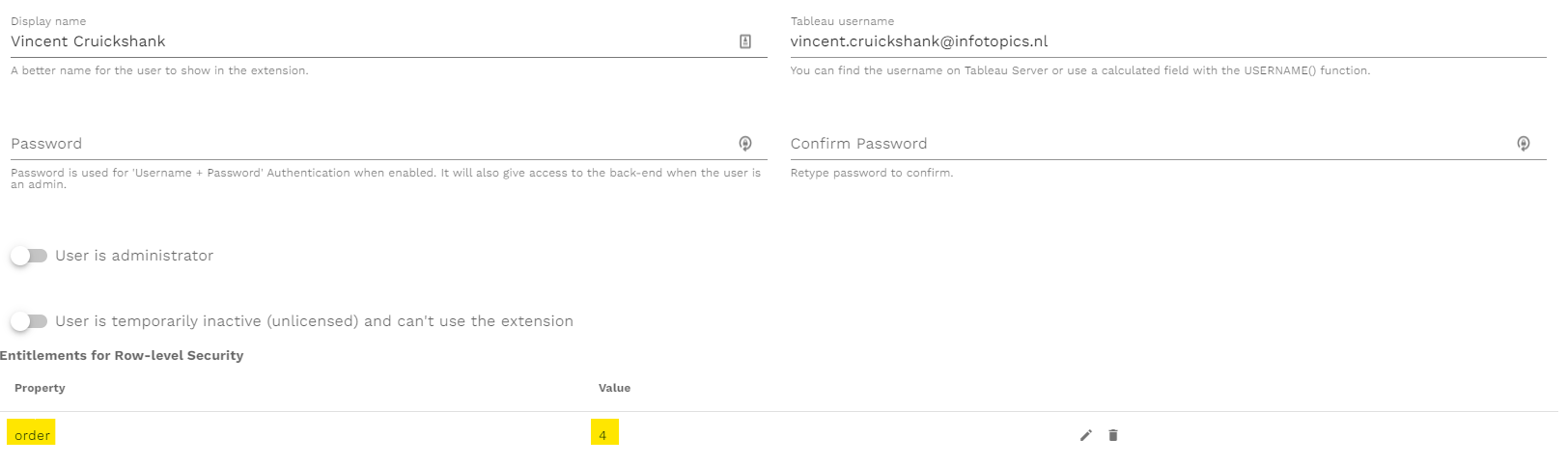
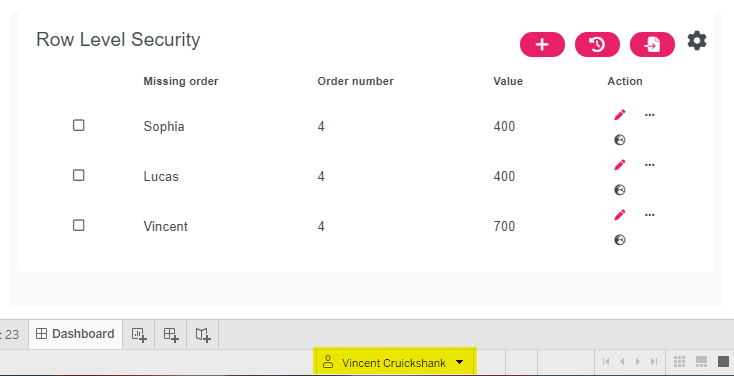
When connected to the schema only the rows will be present in your data set
RLS Entitlement import
For customers that have an existing set of entitlements for their RLS policies we have the following solution to easily import this into WriteBackExtreme. Any ETL tool can be used to populate our internal WriteBackExtreme RLS entitlements table. Since you are already use Tableau we recommend to achieve this with Tableau Prep. In Tableau prep you can transform your entitlement dataset to our data structure for the RLS Entitlements. After setting up this prep, you can easily add it as a scheduled task in your tableau server instance. As an example we have created a sample file that can be used as an inspiration.
The most important of the prep is that you need to populate the _rls_entitlements table. The following columns need to be populated:
assignable_type (this needs to be
userorgroupsince we can set entitlements for groups or for users.assignable_id (the id of the user or the group) (note that this should be our internal id in the
_usersor_groupstable)property (the name of the entitlement)
value (the value of the entitlement)
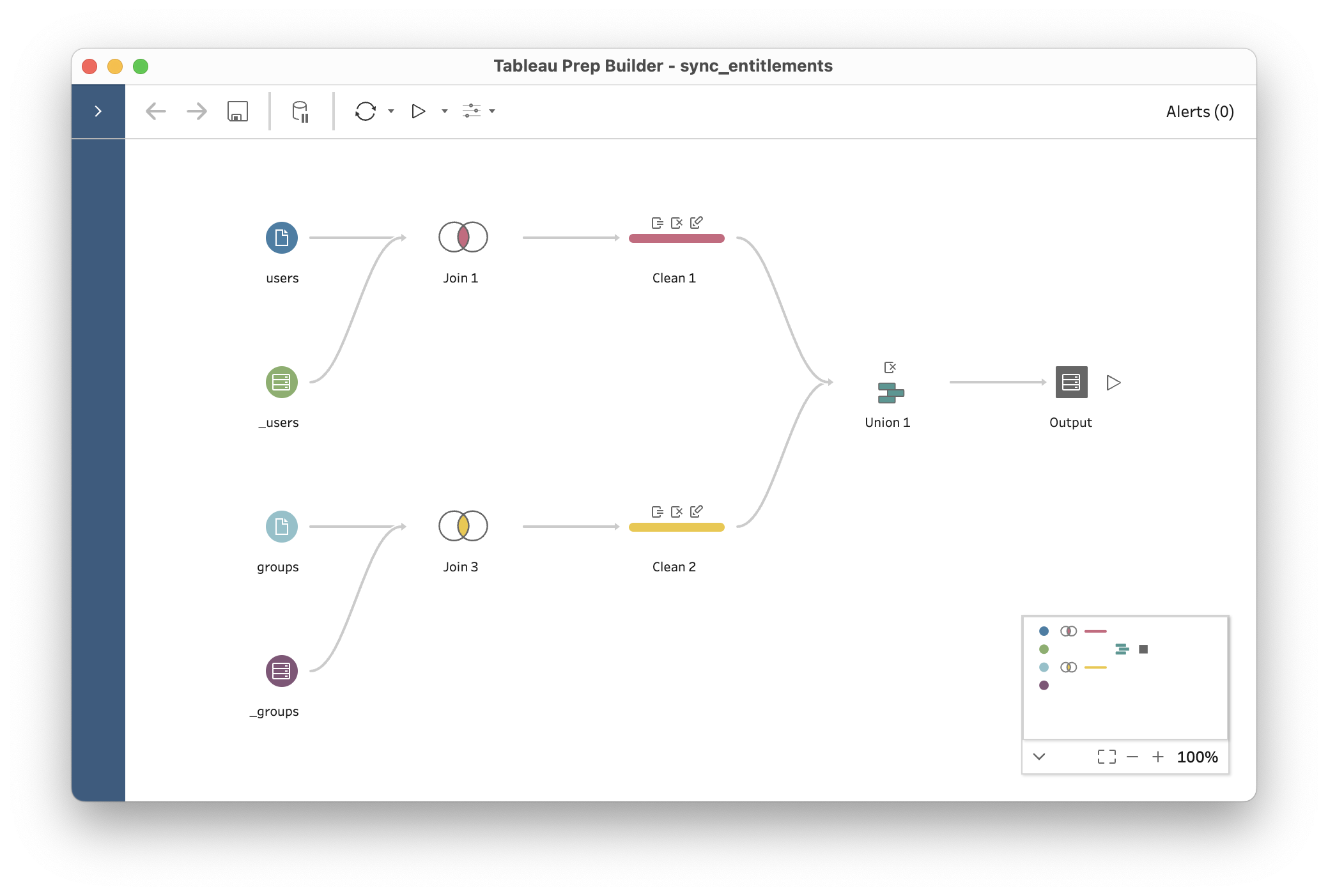
Want to try it yourself? Use our example files as inspiration!
Last updated
Was this helpful?
